External Redirect Hosts
For security reasons, LabKey Server restricts the host names that can be used in returnUrl parameters. By default, only redirects to the same LabKey instance are allowed. Other server host names must be specifically granted access to allow them to be automatically redirected.
For more information on the security concern, please refer to the
OWASP advisory .
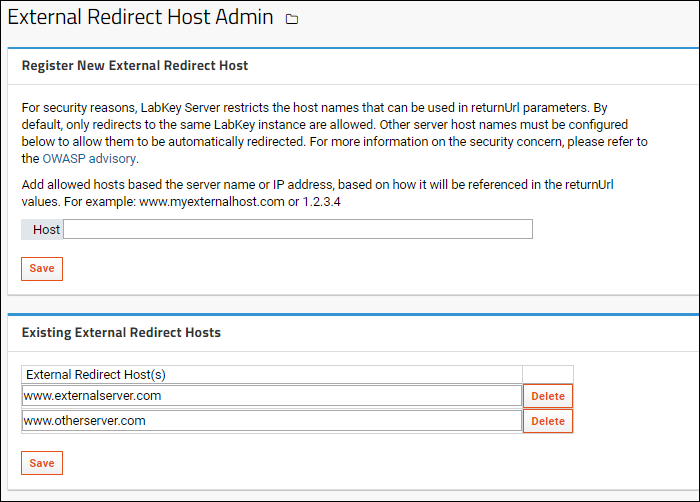
A site administrator can allow hosts based on the server name or IP address, based on how it will be referenced in the returnUrl parameter values.
To add an External Redirect Host URL to the approved list:
- Go to > Site > Admin Console.
- Under Configuration click Allowed External Redirect Hosts.
- In the Host field enter an approved URL and click Save.
- URLs already granted access are added to the list under Existing External Redirect Hosts.
- You can directly edit and save the list of existing redirect URLs if necessary.
Allowed External Resource Hosts
The
Register New External Resource Host panel will show details about the specific CSP configured on this server. Learn more here:
Content Security Policy.
The standard LabKey CSP restricts hosts that browsers can use as resource origins. By default, only sources from this server are allowed; other server hosts must be configured below to enable them to be used as external sources. All provided hosts are added into the CSP using the ${} substitution key shown next to each directive.
As one example, a "connect-src" directive would be needed to support a script tag like the following in an page or wiki:
<script src="www.externalserver.com/script.js" />
To allow a resource, pick a directive and add the associated hostname or IP address, for example: www.myexternalhost.com or 1.2.3.4.
To add an allowed resource host to the approved list:
- Go to > Site > Admin Console.
- Under Configuration click Allowed External Resource Hosts.
- Select the desired directive:
- connect-src
- font-src
- frame-src
- image-src
- object-src
- script-src
- style-src
- In the Host field enter an approved hostname or IP address and click Save.
- URLs already granted access are shown on the list under Existing External Resource Hosts.

External sites added as sources will be allowed as elements in the
content security policy, making it possible for clients to avoiding needing a custom CSP for allowing these sources.
Find
examples in that topic.
Related Topics
