Central Authentication Service (CAS) is a ticket-based authentication protocol that lets a user sign on to multiple applications while providing their credentials only once to a centralized CAS server (often called a "CAS identify provider"). Enabling CAS authentication lets LabKey Server authenticate users using a CAS identity provider, without users providing their credentials directly to LabKey Server. Learn more in the
CAS Protocol Documentation .
You can also configure LabKey Server itself as a CAS Identity Provider, to which other servers can delegate authentication. For details see
Configure CAS Identity Provider.
Note that
basic HTTP authentication and
netrc authentication using usernames are not compatible with SSO authentication such as CAS.
API keys can be used as an alternative for authenticating during LabKey API use.
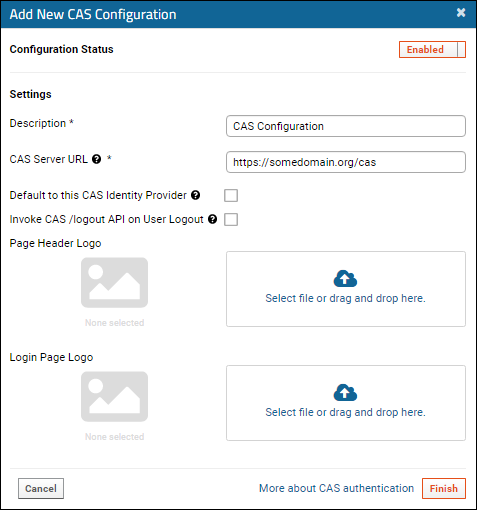
Add/Edit a CAS Single Sign-On Configuration
- Select > Site > Admin Console.
- Under Configuration, click Authentication.
- In the Configurations section, Primary tab, select Add New Primary Configuration > CAS....

- In the popup, enter the following:
- Configuration Status: By default, new configurations are Enabled. Click the slider to disable it.
- Name/Description: Enter a unique name for this configuration to clearly differentiate it from other authentication configurations, especially if you configure multiple CAS configurations. This will appear in the settings UI and in the audit log every time a user logs in using this configuration.
- CAS Server URL: Enter a CAS server URL. The URL should start with "https://" and end with "/cas"
- Default to this CAS configuration: Check the box to redirect the login page directly to the configured CAS server instead of requiring the user to click on a logo.
- Invoke CAS /logout API on User Logout: Check the box if you want a user logging out of this server to also invoke the /logout action on the CAS identity provider. Otherwise, logout on a server using CAS does not log the user out of the CAS identity provider itself.
- Associated Email Domain: Email domain that indicates which users are expected to authenticate using this configuration. For example, if set to 'labkey.org', all users who enter xxxxxx@labkey.org are presumed to authenticate using this configuration. This is often left blank, but if provided, LabKey will suggest this authentication method to users with the specified domain if they fail an authentication attempt using a different configuration. LabKey will also not create database logins when administrators add user accounts with this email domain.
- Login Page Logo & Page Header Logo: Logo branding for the login UI. See examples below.
- Click Finish.
Note that you can save a partially completed CAS configuration provided it is disabled. Any fields provided must be valid, but if you see errors when saving, you can save work in progress in a disabled state and return to complete it later.
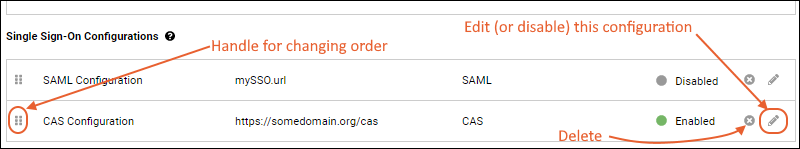
You will see your new configuration listed under
Single Sign-On Configurations. If there are multiple configurations, they will be listed in the interface in the order listed here. You can use the six-block handle on the left to drag and drop them to reorder.
Auto Create Authenticated Users
If a user is authenticated by the CAS server but does not already have an account on the LabKey Server, the system can create one automatically. This is enabled by default but can be disabled using a
checkbox in the global settings of the authentication page
Edit/Disable/Delete CAS Configurations
On the list of
Single Sign-On Configurations you will see the CAS configuration(s) you have defined, with an enabled/disabled indicator for each.
- Use the six-block handle to reorder single sign-on configurations.
- Use the to delete a configuration.
- To edit, click the (pencil) icon.
After making changes in the configuration popup, including switching the
Enabled slider on or off, click
Apply to exit the popup and
Save and Finish to close the authentication page.
Single Sign-On Logo
For CAS, SAML, and other single sign-on authentication providers, you can include logo images to be displayed in the
Page Header area, on the
Login Page, or both. These can be used for organization branding/consistency, signaling to users that single sign-on is available. When the logo is clicked, LabKey Server will attempt to authenticate the user against the SSO server.
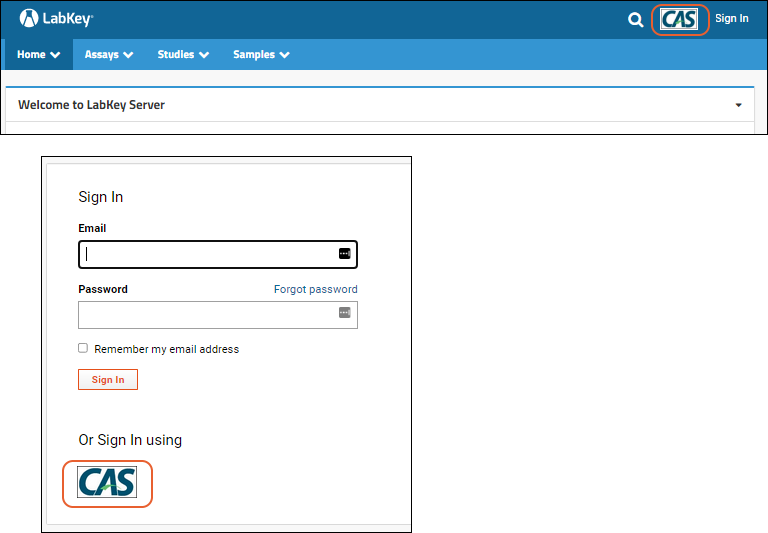
If you provide a login page logo but no header logo, for example, your users see only the usual page header menus, but when logging in, they will see your single sign-on logo.
Related Topics

 Note that you can save a partially completed CAS configuration provided it is disabled. Any fields provided must be valid, but if you see errors when saving, you can save work in progress in a disabled state and return to complete it later.
Note that you can save a partially completed CAS configuration provided it is disabled. Any fields provided must be valid, but if you see errors when saving, you can save work in progress in a disabled state and return to complete it later. After making changes in the configuration popup, including switching the Enabled slider on or off, click Apply to exit the popup and Save and Finish to close the authentication page.
After making changes in the configuration popup, including switching the Enabled slider on or off, click Apply to exit the popup and Save and Finish to close the authentication page.